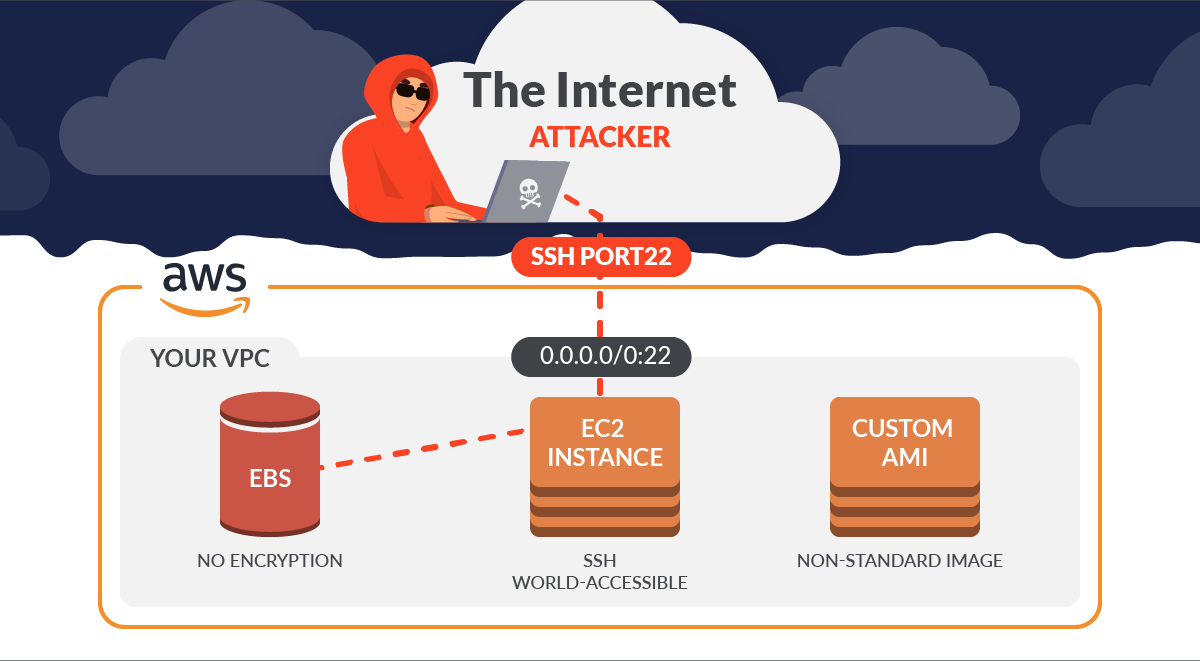
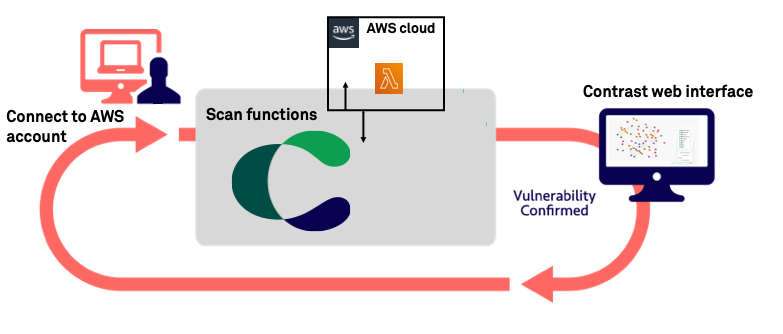
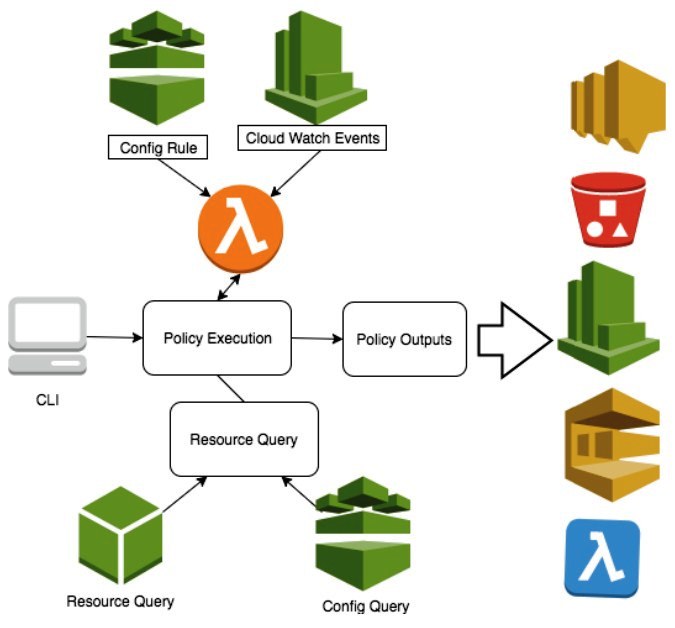
Automate vulnerability management and remediation in AWS using Amazon Inspector and AWS Systems Manager – Part 1 | AWS Cloud Operations & Migrations Blog

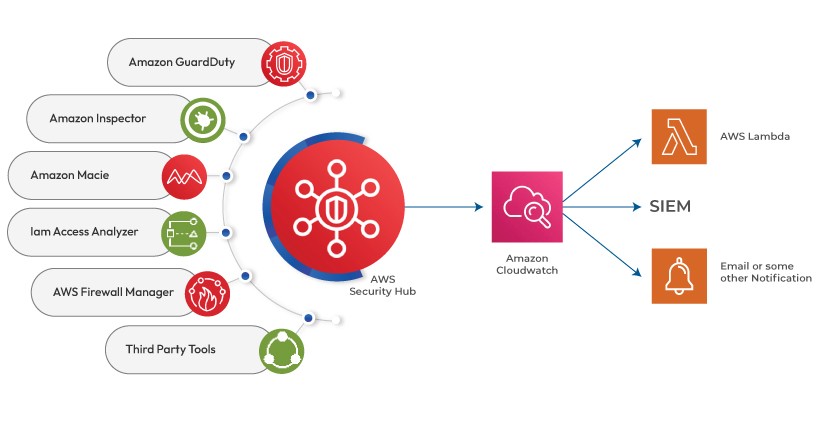
Amazon S3 Malware Scanning Using Trend Micro Cloud One and AWS Security Hub | AWS Partner Network (APN) Blog
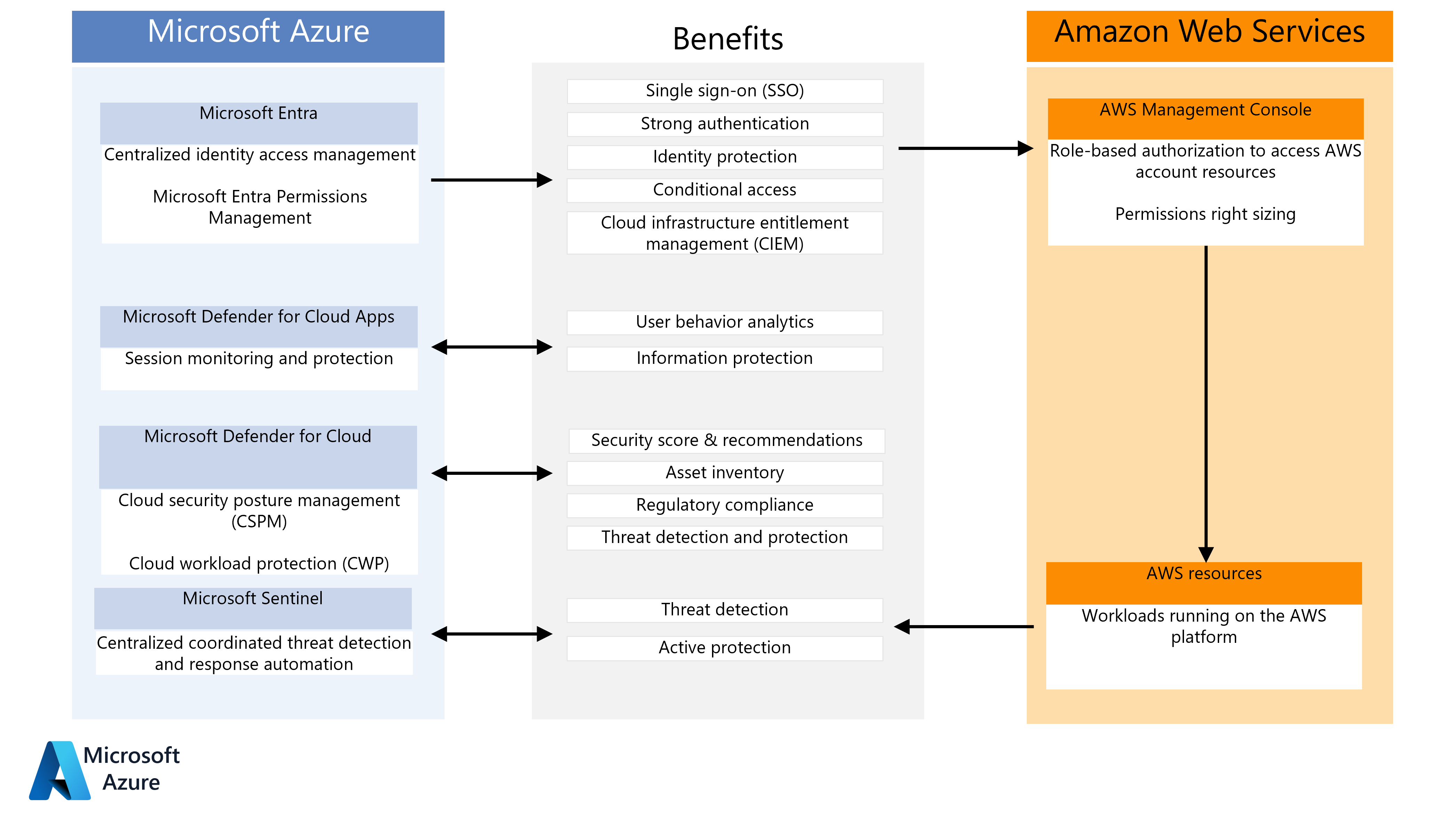
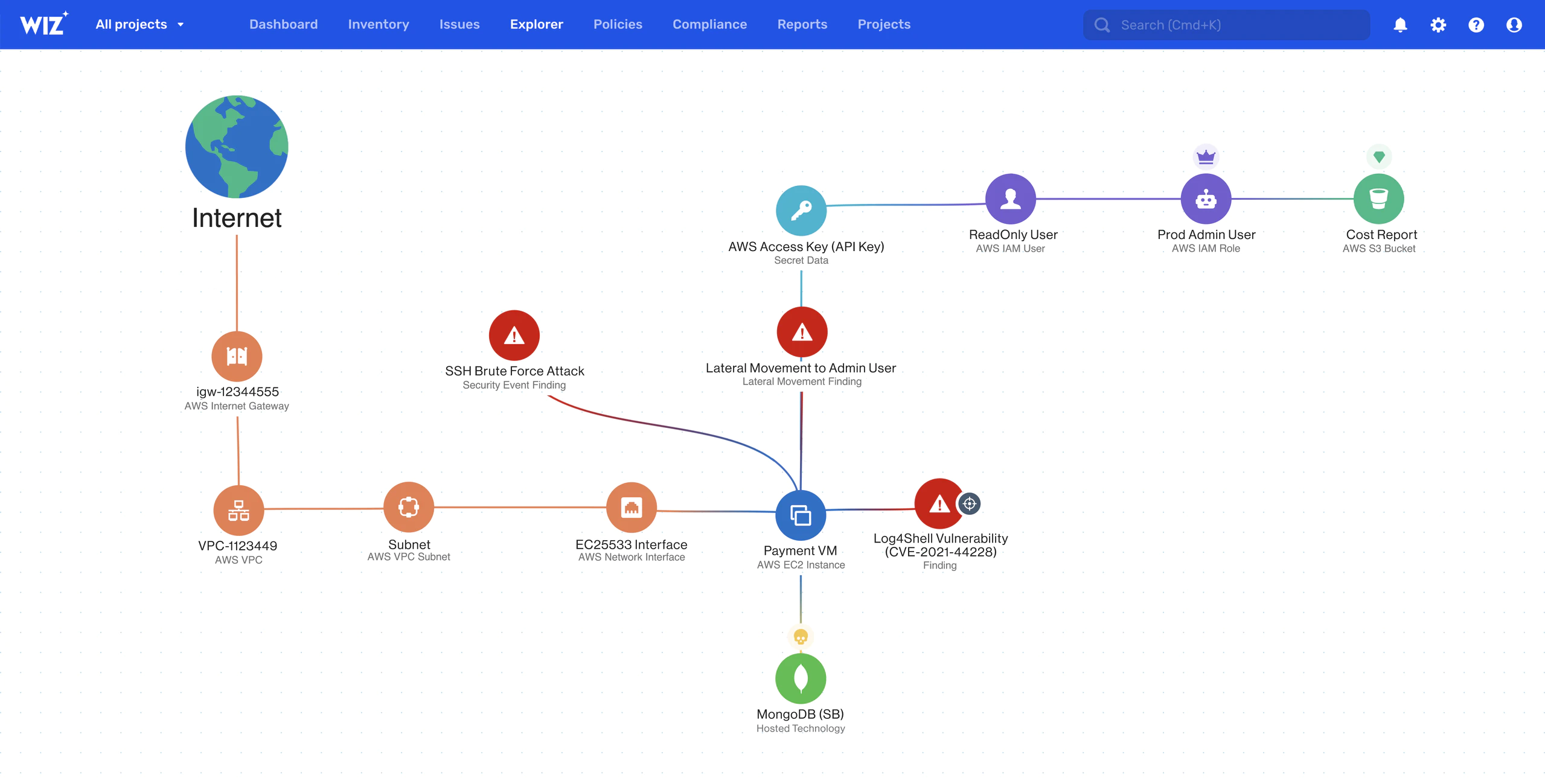
Defender for Cloud Apps and Microsoft Sentinel for AWS - Azure Architecture Center | Microsoft Learn

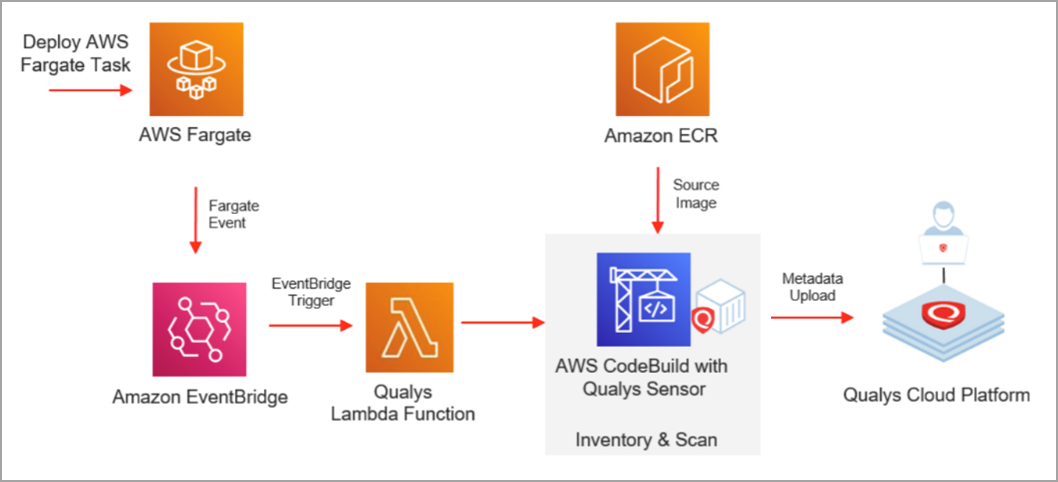
Scanning Docker Images for Vulnerabilities using Clair, Amazon ECS, ECR, and AWS CodePipeline | AWS Compute Blog