
How Secret Recovery Phrases Work. Understand the mystical secret words… | by Ernesto Ojeda | Neftify | Medium

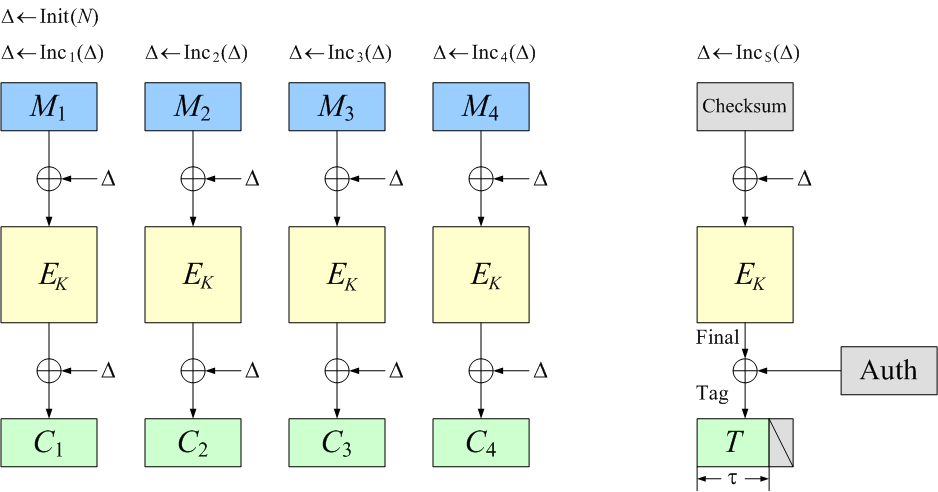
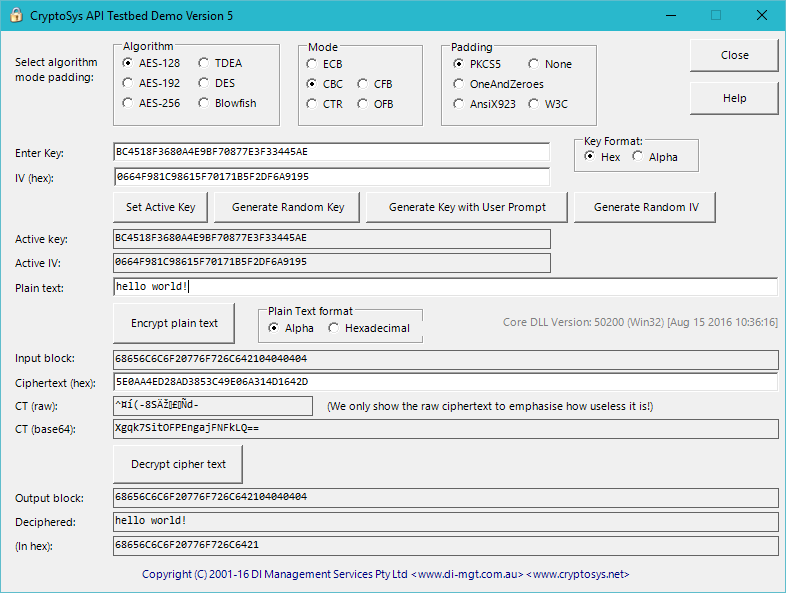
Encrypting Data with Golang. 3dfosi/gocrypt — A Golang Encryption… | by Jeremy Cheng | Level Up Coding

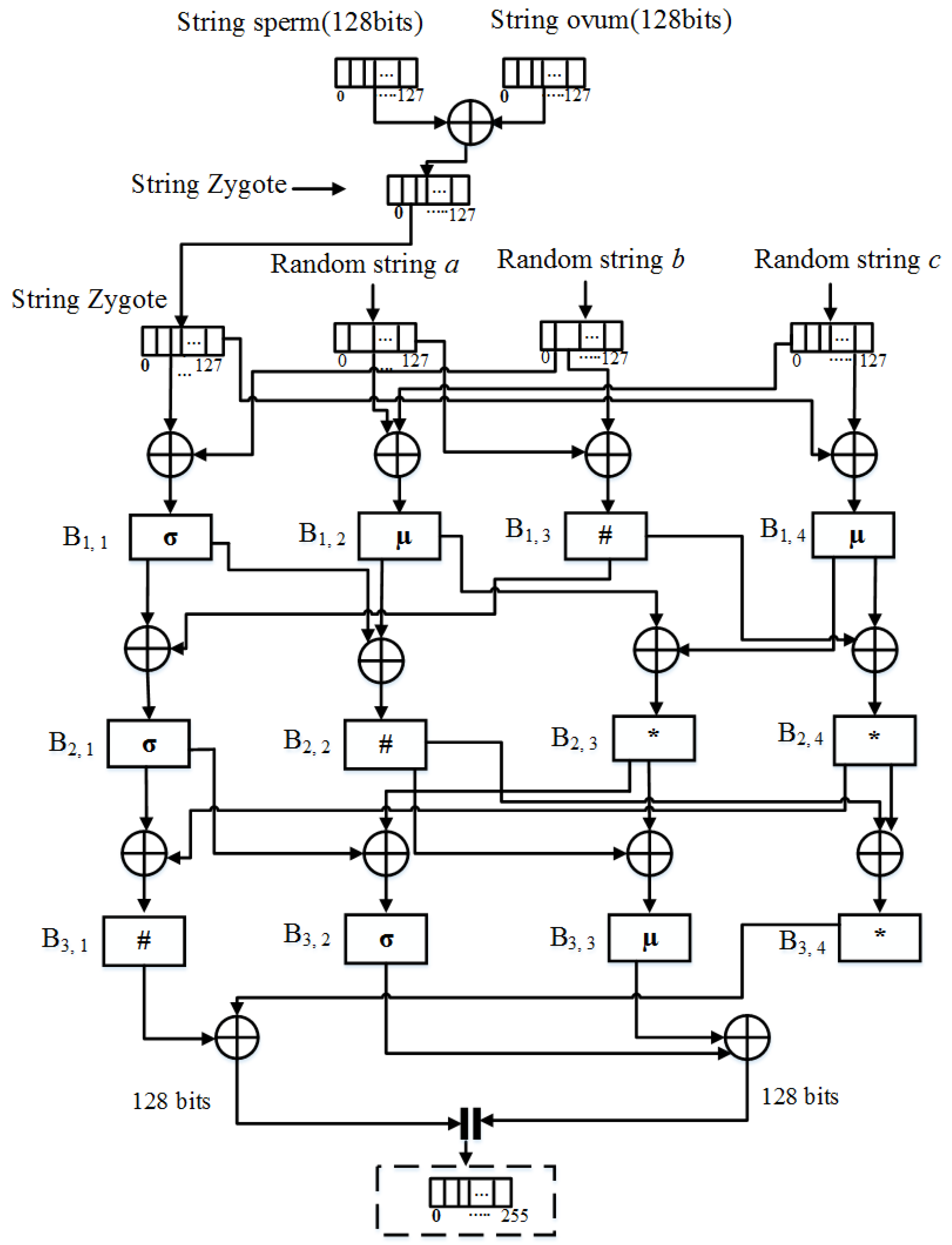
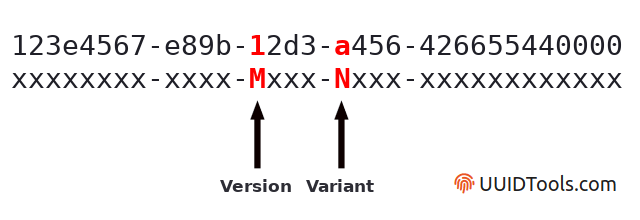
An example of a 36-character string depicting a 128-bit binary value in... | Download Scientific Diagram






![java - String vs char[] - Stack Overflow java - String vs char[] - Stack Overflow](https://i.stack.imgur.com/WhEBr.png)

